Updated: January 11, 2025
Contents
- Major SaaS security concerns putting your solution at stake
- 9 SaaS security best practices to fortify your software
- Checklist on how to secure SaaS applications: *instinctools edition
- SaaS security standards put into action: legacy software modernization for a licensing company
- Securing SaaS isn’t a one-and-done endeavor — it’s a continuous process
- FAQ
Key highlights
- From misconfigurations to regulatory hurdles, there are plenty of SaaS security challenges to deal with, but all of them can be covered if you follow a battle-proven SaaS application security checklist.
- Security standards for SaaS applications in focus: *instinctools’ tech lead shares the best practices and tips for safeguarding your software.
- The game-changing role of AI tools in adopting a proactive security strategy.
Threads as trivial as data breaches, data leakage, and unauthorized access keep ranking among the top security incidents the quarter of software as a service providers experienced in 2024. How do you ward off these hurdles in 2025 and beyond?
Our experts in SaaS security posture management highlight common chinks in the armor of the on-demand solutions and share a battle-proven SaaS security checklist for tackling them with industry best practices.
Major SaaS security concerns putting your solution at stake
Just as the chain is only as strong as its weakest link, it plays out the same way for software as a service security in cloud computing. Here are the five most common SaaS threats that can imperil the overall security level of software applications.
- Misconfiguration as a primary reason for data breaches remains the biggest cloud security risk organizations have to face. When security teams fail to configure SaaS software appropriately, or too many roles within the company have access to the SaaS security controls, it can lead to exposing customer data, its leakage, or theft.
- Insecure APIs. Jeopardizing the APIs’ security is the second largest of all OWASP API risks. Session tokens in URLs can be leveraged by cyber attackers, resulting in unauthorized access to SaaS data or a data breach.
- Unauthorized access. A lack of data encryption and irresponsible key management can also have dire consequences, such as exposing confidential data and personally identifiable information that your customers have entrusted you as their SaaS vendor. Sometimes unauthorized access can take a toll on your business, as happened to LastPass after two security breaches in 2022.
- Cloud infrastructure issues. Inadequate security of cloud components, such as physical and virtual servers, network perimeter, etc., makes your software an easy target for cyber attacks.
- Inability to meet regulatory requirements. Сomplying with international and industry-specific regulations is a must for software providers. However, undergoing ISO certification or covering HIPAA SaaS compliance, etc. is easier said than done. Such challenges are usually put off until the eleventh hour.
9 SaaS security best practices to fortify your software
Based on the major SaaS vulnerabilities mentioned earlier, *instinctools’ experts have identified security practices to follow so that your product’s safety won’t hinder customer adoption.
1. Adopt security-first mindset within the company
Keeping an eye on security risks from the very beginning of the product development and monitoring security threats through real-time discovery after the solution’s rollout is the surest way to ward off most of the SaaS security issues.
Shifting security left, to the software development life cycle (SDLC), can be done by leveraging the DevSecOps approach. To hone your security level without sacrificing deployment speed, we advise you to bank on:
- Threat modeling to uncover weak points and critical vulnerabilities in your solution before they turn into real SaaS threats.
- Automated security testing to get a static, dynamic, and interactive CI/CD pipeline security analysis.
Adopting a security-first mindset goes beyond integrating DevOps practices right from the start of product development. It’s also about raising security consciousness and regular security awareness training among employees outside security teams. You can minimize the likelihood of data breaches, sensitive data exposure, and other security incidents by educating your staff on malware, phishing, social engineering attacks, etc.
For instance, make a habit of conducting phishing simulations. Alarming statistics indicate that in 2024, 71% of companies experienced at least one successful phishing attack. Running phishing simulations to check how your staff acts when receiving phishing-like emails is a way to raise their awareness of possible threats and practice the algorithm of identifying and reporting the threat effortlessly.
Strengthening an organization’s overall security posture is especially crucial if you follow the work-from-home trend adopted by 67% of software companies worldwide and allow your staff to work fully or mostly remotely. Software as a service vendors have to monitor employees’ devices and guard their organization’s data with a comprehensive BYOD (bring your own device) policy as part of their SaaS security requirements. For instance, to perfect SaaS data security within the company, the following can be done:
- Leverage SSL certificates to ensure secure connection for your employees anywhere anytime;
- Stipulate automated wiping of data on the staff’s devices after failed login attempts.
Hone your SaaS risk management with our support
2. Stay compliant with all the necessary industry and location-specific regulations
Legal compliance isn’t just a best practice, it’s a requirement for SaaS providers. Following industry-specific world-wide and local regulations can be worth a thousand words if you want to prove your reliability to potential SaaS customers.
For example, if US-based vendors offer their software to EU-located clients, they should stay compliant not only with GDPR but also with local regulations, such as the Data Governance Act (DGA), ePrivacy Directive, Open Data Directive, to name a few.
If you provide SaaS industry-specific software, you have to take this into account, as local industry regulations may differ. Let’s take the healthcare sector as an example. In the US, you must add compliance with the HITECH Act and HIPAA SaaS requirements to your security standards as a software provider.
However, if you want to expand your market reach and offer your solution, let’s say, in Canada, you’ll need to follow PIPEDA stipulations. This act is quite similar to HIPAA, but there are still differences, the violation of which can cost you up to $100,000. For instance, PIPEDA applies to all customer data, while HIPAA covers only healthcare-related confidential data.
3. Ensure secure API and authentication
API endpoints’ vulnerabilities and authentication flaws set the stage for unauthorized access to sensitive information.
The fewer API keys you have, the less is the probability of an API-related incident. If this approach is out of options, rotate API keys at least annually.
— Dzmitry Danskoi, Tech Lead, *instinctools
What else can be done to derisk customer data? Build multifactor authentication (MFA) in your software. It’s one of the standard SaaS authentication methods that shields personal and sensitive data from falling into the wrong hands. However, going through it every time when opening an app can become a burden for end users.
You can simplify SaaS data protection without compromising security by providing customers with a single sign-on (SSO) option when they can safely log in to the system with their company’s Google, Microsoft, etc. accounts. For instance, OAuth 2.0 protocol is one of the widespread ways to simplify user access to the scads of a company’s apps.
Just as MFA and SSO are must-have preventive measures to implement in your SaaS solution, they’re also critical to adopt within your company, where the software is being crafted. Neglecting these security standards puts the safety of your SaaS users’ data at stake.
For instance, your employees should be aware that cybercriminals can bombard them with fake MFA push notifications to compromise their accounts, as it happened with SolarWinds. The corporation’s security structure was busted because employees routinely approved a push notification — essentially, the company’s staff invited the attackers to the system’s core. Therefore, if your SaaS solution is targeted at companies related to healthcare, finance, or politics, you shouldn’t take MFA lightly or let approving push notifications become staff’s “second nature.”
Keep the bar of your SaaS network security high
4. Bring efficient IAM controls
In the SaaS development process, robust authentication goes hand in hand with solid identity and access management (IAM). Efficient IAM controls empower SaaS providers to:
- Log and monitor all access attempts to have complete visibility across the system and spot attackers right off the bat.
- Set different user access rights within the company based on their role (RBAC), identity (IBAC), or attributes (ABAC).
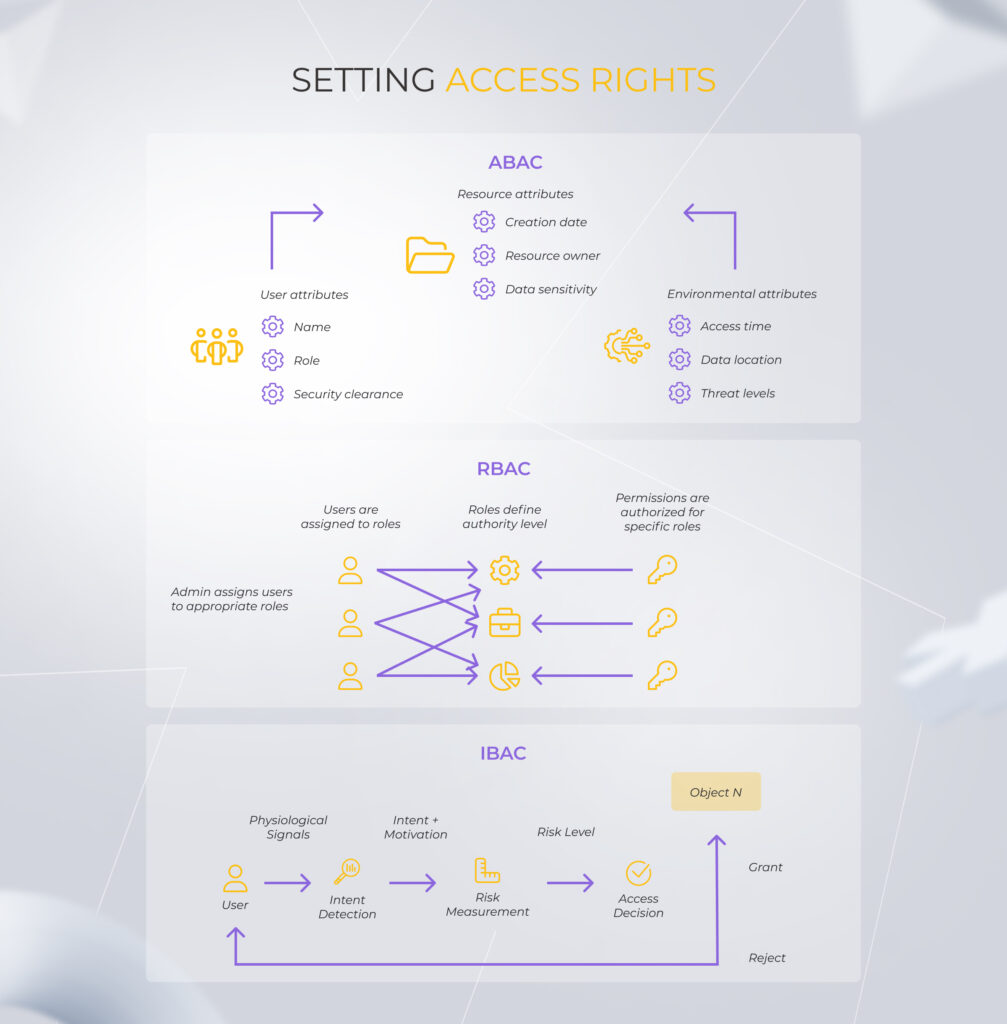
However, consider that any control over data access, processing, and monitoring impacts the system’s performance. More importantly, each security enhancement increases the solution’s complexity for end users. As a SaaS provider, you have to juggle one and the other to provide customers with user-friendly software while keeping their confidential data safe.
Stop intruders at the front door
5. Make robust data encryption a table stake
Data protection regulations such as GDPR, D-DPA, etc., impose restrictions on using customers’ personally identifiable information for decision-making. Therefore, you’ll need to leverage encryption techniques such as data scrambling and data substitution to ensure users’ anonymity, while still being able to know your customers better. With such an approach, personal data is modified to ensure that it cannot be matched to individuals. However, you still can effectively use this anonymized data to analyze, for example, a product’s popularity in different regions.
SaaS data protection entails a greater responsibility level, than in the IaaS model, where encryption is a customer’s duty.
As a SaaS vendor, you should bet on symmetric or asymmetric encryption to get control of sensitive data, whether it’s at rest, in use, or in motion. With symmetric encryption, the same key per session is used for encryption and decryption. While an asymmetric method implies two encryption keys – public for data encryption and private for its decryption.
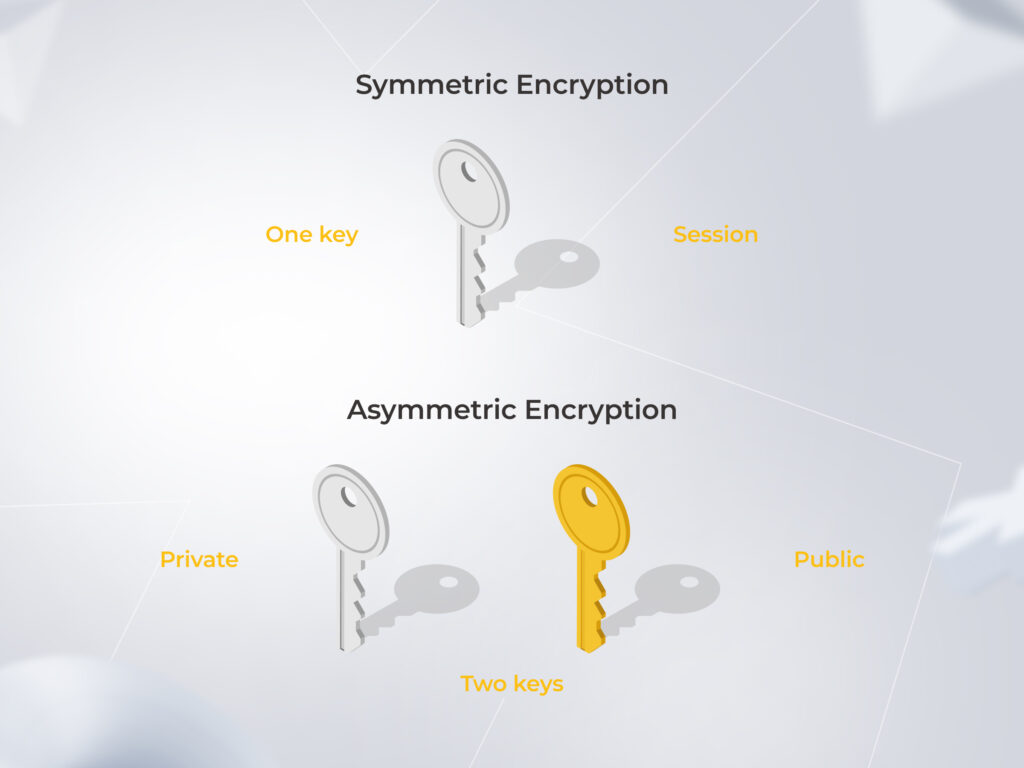
These are the protocols you can leverage to secure data in its different states:
- TLS (Transport Layer Security) and SSL (Secure Sockets Layer) for the data in motion. Guard emails, files, etc., moved between applications, networks, computers, etc. And no matter how trivial it may seem, if your solution is web-based, use HTTPS (Hypertext Transfer Protocol Secure) protocol to minimize risks.
- Secure Encrypted Virtualization (SEV) for the data in use. Defend data storage and files that are currently open.
- Advanced Encryption Standard (AES) for the data at rest. This protocol is a top choice for safeguarding databases, cloud storage assets, and file archives.
Ensuring timely updates of these encryption protocols should be on your SaaS checklist.
6. Run regular security audits
Data encryption means performing regular audits, both internal and external, as part of your SaaS data encryption strategy. Knowing the potential risks of your software and understanding how to nip them in a bud can help you become a more reliable vendor for your SaaS customers. Auditing your solution lets you catch sight of minor issues before they turn into a real threat looming over your solution.
What are the vital components of an efficient security audit? Instinctools’ experts gear you up with the most essential steps of a SaaS audit checklist:
- Review your security policies, standards, and procedures. Inspect the encryption protocols you use for the data in motion, in use, and at rest, and evaluate how well they do their job. For example, if you use DES (Data Encryption Standard) to secure sensitive information at rest, it may be time to switch to a more sophisticated AES protocol. Another best practice is performing malware checks on files before importing or uploading data to the cloud when running a cloud SaaS security assessment.
- Check your coding. Don’t underestimate the importance of secure coding standards. Measuring code quality is an integral part of SaaS security assessment that implies reviewing its efficiency, security, reliability, and maintainability. If one of these parameters has weak spots, for example, you uncover missing initialization, it puts the whole SaaS solution at risk.
- Perform various security tests. If you want to comply with regulations such as HIPAA, ISO, IEC, SOC 2, etc., you’ll need to undergo a lot of security tests, including vulnerability scanning, security assessment, penetration tests, and compliance audit. Thereby you’ll prove the solid security level of your solution.
It’s also important to distinguish between internal and external security audits.
- Internal audits depend mostly on your capacity – you can run them whenever you have spare time and free hands.
I’d suggest setting an automated trigger for such audits and conducting them before every solution’s update and release of a new feature.
— Dzmitry Danskoi, Tech Lead, *instinctools
- External audits, on the contrary, are performed by specialized third-party organizations, require a sizable chunk of your budget, and take at least several weeks. Therefore, act according to your industry’s SaaS considerations.
As a SaaS provider, who wants to safeguard their solution from external and insider threats, you can require a security audit for any third-party software integrating with your application to mitigate security risks.
7. Provide a comprehensive disaster recovery plan
SaaS risk assessment during a security audit leads to developing incident response and disaster recovery plans as security measures to tackle outages and other issues if they happen. You should ensure data backups are in place and easily accessible to minimize operational disruption when disaster strikes and enable business continuity even in the case of major security blunders.
As a SaaS vendor, you have to provide your clients with a disaster recovery plan that meets two performance goals agreed upon with the customer:
- Recovery Point Objective (RPO). This measure determines the amount of data that could be lost in an incident. For example, it can be data for the last 15 minutes.
- Recovery Time Objective (RTO). This standard describes how much time you’ll need to recover the lost data. For example, you can set one week for the task.
Having a solid recovery plan doesn’t guarantee that all team members know their roles and responsibilities during an actual incident. Practice makes perfect, that’s why we recommend running disaster recovery drills to test your ability to recover and restore data and systems after a disruption. That way, you minimize downtime and the probability of data loss during a real disaster and ensure compliance with industry standards.
— Dzmitry Danskoi, Tech Lead, *instinctools
Want to be fully armored for disaster recovery?
8. Take advantage of AI tools
Organizations get used to relying on artificial intelligence technology, and SaaS companies are no exception. For instance, AI tools leveled up the ability to spot and analyze suspicious patterns in real time, enabling software providers to adopt a truly proactive security posture.
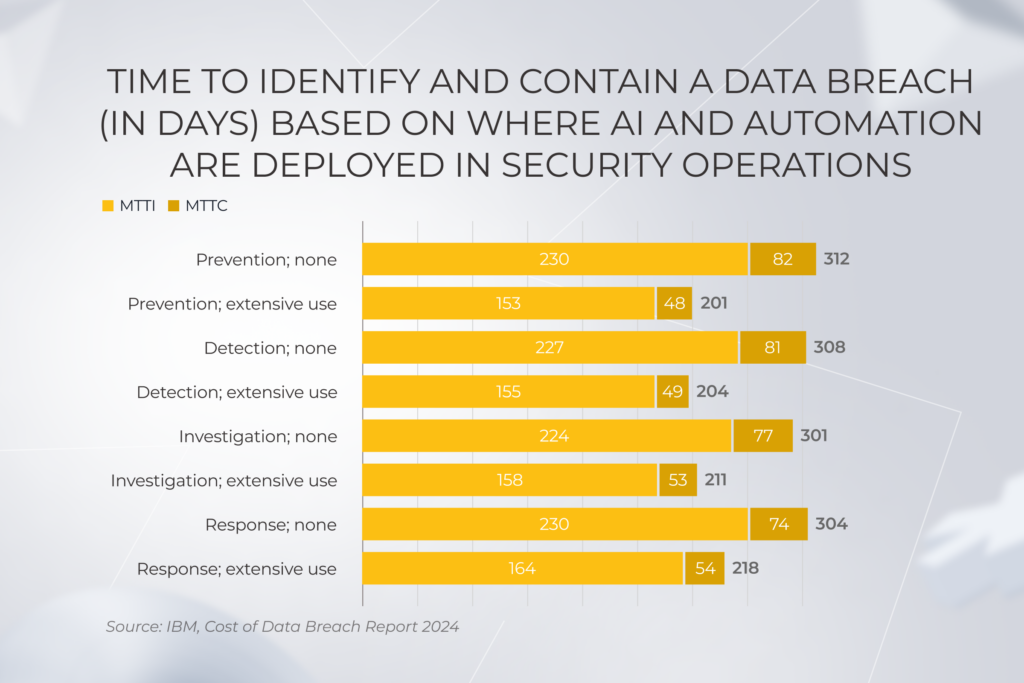
AI-driven automation became another heavy hitter reshaping the ways vendors perform routine tasks to ensure the security of their SaaS data. As for 2024, 27% of companies entrusted AI with anomaly and incident detection, prevention, investigation, and response.
In my practical experience, AI software is the most efficient in threat detection. With it, tasks such as vulnerability scanning, prioritizing perils depending on their potential impact, and threat reporting can be fully automated, freeing your employees’ working hours for more challenging assignments.
— Dzmitry Danskoi, Tech Lead, *instinctools
While some companies question the safety of implementing AI automation, others reap its benefits, accelerating time for prevention, detection, investigation, and response to data breaches by a third.
9. Leverage expert support
93% of organizations are moderately to extremely concerned with the shortage of experienced security aces. Even if you are among the lucky 7% with vetted pros on their in-house IT team, you can lack specific expertise to deal with SaaS security monitoring. Or you may need a safe pair of hands to get over mind-boggling security audits before obtaining compliance with new regulation requirements. Don’t hesitate to reach out to skilled professionals.
Get your SaaS security on lock
Checklist on how to secure SaaS applications: *instinctools edition
As you can see, once you follow SaaS security best practices and rely on battle-tested expertise, managing SaaS security challenges will no longer seem daunting and overwhelming. We’ve summarized the best practices and security measures to focus on.

SaaS security standards put into action: legacy software modernization for a licensing company
While data security is crucial for any software vendor, it’s a matter of reputation for a global security tech provider. Our client needed to hone SaaS security compliance to obtain ISO 27001 certification stress-free.
The tech stack of their licensing software, created in the aughts, became partly outdated. SOAP API and legacy Apache products, such as the Axis2 framework and the TomEE 7 application server, called for present-day replacements.
We opted for a gradual modernization approach to minimize the resistance to change from the client’s in-house team, which had stayed the same for over 30 years. The shift from TomEE 7 to TomEE 8 and from Axis2 to CXF went smoothly, paving the road to the future adoption of the industry standard, the Spring framework. We also conducted code refactoring and wiped out bugs in the client’s testing system to simplify software upkeep.
Get more details on the story
Securing SaaS isn’t a one-and-done endeavor — it’s a continuous process
Since security is one of the SaaS trends that are here to stay, as a SaaS vendor, you should amp up the security level of your solution. But consider that the diversity of security requirements for SaaS applications doesn’t allow you to stir risks away one by one. For example, you can’t state providing efficient IAM controls without secure APIs, just as running regular security audits makes no sense if it doesn’t lead to creating a robust disaster recovery plan. Therefore, you should address all these issues holistically.
Want to get rid of SaaS security concerns and craft fail-safe software?
FAQ
SaaS security policy covers compliance with security regulations, authentication methods, identity and access management, types of data encryption, security audits frequency, and disaster recovery plan. It should be comprehensive enough to serve as a basis for your SaaS security strategy.
The four SaaS security issues you should address in the first place are misconfigurations, insecure APIs, unauthorized access, and reaching regulatory compliance. All of them can be dealt with by following industry standards for data security — security-first mindset, compliance with industry- and country-specific regulations, secure APIs, IAM controls, data encryption, regular audits, AI-powered threat detection, data recovery plan, and reaching out to security professionals.
Primary measures for securing SaaS applications are:
– Establishing protected cloud environments
– Having robust security protocols and data encryption algorithms
– Keeping a weather eye on user authentication and access control
– Providing solid incident response and data recovery plans